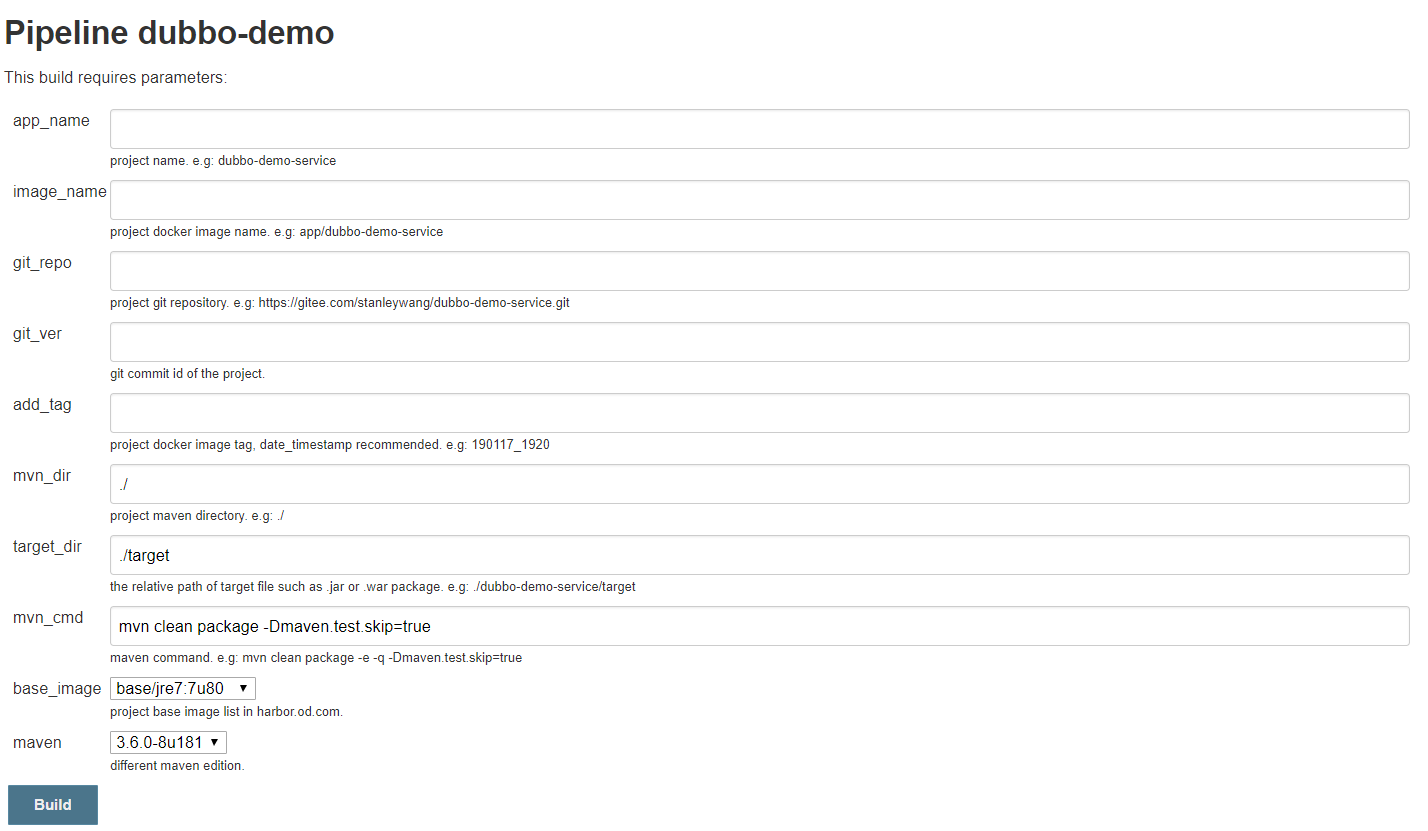
欢迎加入王导的VIP学习qq群:==>932194668<==
OSI七层模型
OSI模型(Open System Interconnection Model)是一个由ISO提出得到概念模型,试图提供一个使各种不同的的计算机和网络在世界范围内实现互联的标准框架。
分层结构
OSI参考模型采用分层结构,如图所示。 不得不说,这张图真的超经典呀。一张图搞定你你不懂的一切。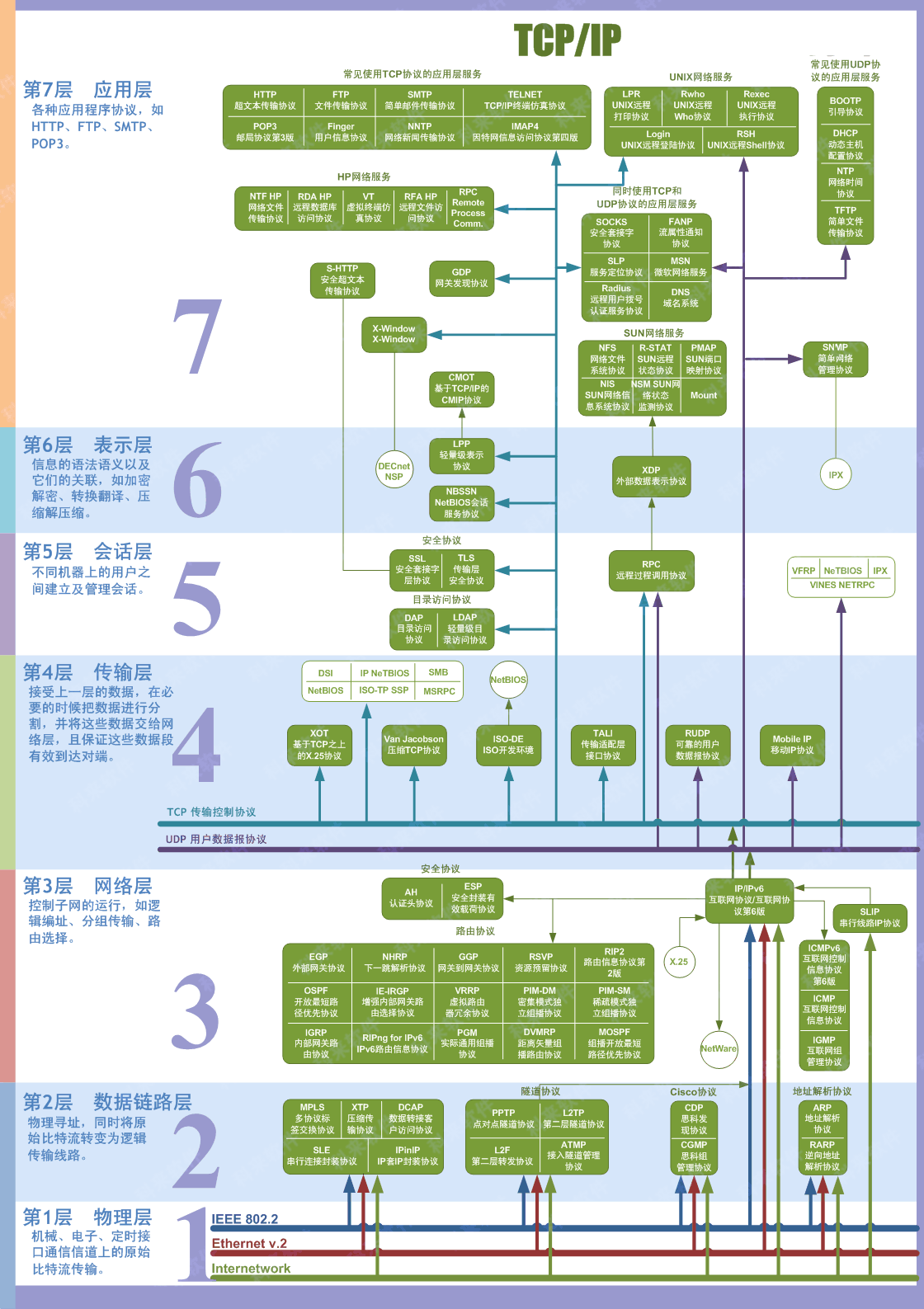
主要分为以下七层(从下至上):物理层、数据链路层、网络层、传输层、会话层、表示层、应用层。
各层功能
- 物理层
简单的说,物理层(Physical Layer)确保原始的数据可在各种物理媒体上传输。在这一层上面规定了激活、维持、关闭通信端点之间的机械特性、电气特性、功能特性以及过程特性,为上层协议提供了一个传输数据的物理媒体。这一层传输的是bit流。 - 数据链路层
数据链路层(Data Link Layer)在不可靠的物理介质上提供可靠的传输。该层的作用包括:物理地址寻址、数据的成帧、流量控制、数据的检错、重发等。这一层中将bit流封装成frame帧。 - 网络层
网络层(Network Layer)负责对子网间的数据包进行路由选择。此外,网络层还可以实现拥塞控制、网际互连等功能。在这一层,数据的单位称为数据包(packet)。 - 传输层
传输层是第一个端到端,即主机到主机的层次。传输层负责将上层数据分段并提供端到端的、可靠的或不可靠的传输。此外,传输层还要处理端到端的差错控制和流量控制问题。在这一层,数据的单位称为数据段(segment)。 - 会话层
这一层管理主机之间的会话进程,即负责建立、管理、终止进程之间的会话。会话层还利用在数据中插入校验点来实现数据的同步,访问验证和会话管理在内的建立和维护应用之间通信的机制。如服务器验证用户登录便是由会话层完成的。使通信会话在通信失效时从校验点继续恢复通信。 - 表示层
这一层主要解决用户信息的语法表示问题。它将欲交换的数据从适合于某一用户的抽象语法,转换为适合于OSI系统内部使用的传送语法。即提供格式化的表示和转换数据服务。数据的压缩和解压缩, 加密和解密等工作都由表示层负责。 - 应用层
这一层为操作系统或网络应用程序提供访问网络服务的接口。
各层传输协议、传输单元、主要功能性设备比较
| 名称 | 传输协议 | 主要功能设备/接口 | 主要功能设备/接口 |
|---|---|---|---|
| 物理层 | IEEE 802.1A、IEEE 802.2 | bit-flow | 比特流 光纤、双绞线、中继器和集线器 & RJ-45(网线接口) |
| 数据链路层 | ARP、MAC、 FDDI、Ethernet、Arpanet、PPP、PDN | frame 帧 | 网桥、二层交换机 |
| 网络层 | IP、ICMP、ARP、RARP | 数据包(packet) | 路由器、三层交换机 |
| 传输层 | TCP、UDP | Segment/Datagram | 四层交换机 |
| 会话层 | SMTP、DNS | 报文 | QoS |
| 表示层 | Telnet、SNMP | 报文 | - |
| 应用层 | FTP、TFTP、Telnet、HTTP、DNS | 报文 | - |
关于协议你应该知道这些
以上通过图表、文字向大家阐述了七层模型每一层的具体功能及其相关协议,但知道了这些还不够,你还要知道以下这些。
TCP/UDP
- TCP/UDP是什么?
TCP — Transmission Control Protocol,传输控制协议。
UDP — User Data Protocol,用户数据报协议。- TCP/UDP的区别(优缺点)?
(1)、TCP是面向连接的,UDP是面向无连接的。TCP在通信之前必须通过三次握手机制与对方建立连接,而UDP通信不必与对方建立连接,不管对方的状态就直接把数据发送给对方
(2)、TCP连接过程耗时,UDP不耗时
(3)、TCP连接过程中出现的延时增加了被攻击的可能,安全性不高,而UDP不需要连接,安全性较高
(4)、TCP是可靠的,保证数据传输的正确性,不易丢包;UDP是不可靠的,易丢包
(5)、tcp传输速率较慢,实时性差,udp传输速率较快。tcp建立连接需要耗时,并且tcp首部信息太多,每次传输的有用信息较少,实时性差。
(6)、tcp是流模式,udp是数据包模式。tcp只要不超过缓冲区的大小就可以连续发送数据到缓冲区上,接收端只要缓冲区上有数据就可以读取,可以一次读取多个数据包,而udp一次只能读取一个数据包,数据包之间独立- TCP三次握手过程
STEP 1: 主机A通过向主机B发送一个含有同步序列号的标志位的数据段给主机B,向主机B请求建立连接,通过这个数据段,主机A告诉主机B两件事:我想要和你通信;你可以用哪个序列号作为起始数据段来回应我。
STEP 2: 主机B收到主机A的请求后,用一个带有确认应答(ACK)和同步序列号(SYN)标志位的数据段响应主机A,也告诉主机A两件事:我已经收到你的请求了,你可以传输数据了;你要用哪佧序列号作为起始数据段来回应我。
STEP 3: 主机A收到这个数据段后,再发送一个确认应答,确认已收到主机B的数据段:”我已收到回复,我现在要开始传输实际数据了。这样3次握手就完成了,主机A和主机B就可以传输数据了。
- 注意
此时需要注意的是,TCP建立连接要进行3次握手,而断开连接要进行4次。- 名词解释
ACK: TCP报头的控制位之一,对数据进行确认,确认由目的端发出,用它来告诉发送端这个序列号之前的数据段都收到了。比如,确认号为X,则表示前X-1个数据段都收到了,只有当ACK=1时,确认号才有效,当ACK=0时,确认号无效,这时会要求重传数据,保证数据的完整性。
SYN: 同步序列号,TCP建立连接时将这个位置1。
FIN : 发送端完成发送任务位,当TCP完成数据传输需要断开时,提出断开连接的一方将这位置1。
- TCP可靠性的四大手段
(1)、顺序编号: tcp在传输文件的时候,会将文件拆分为多个tcp数据包,每个装满的数据包大小大约在1k左右,tcp协议为保证可靠传输,会将这些数据包顺序编号
(2)、确认机制: 当数据包成功的被发送方发送给接收方,接收方会根据tcp协议反馈给发送方一个成功接收的ACK信号,信号中包含了当前包的序号
(3)、超时重传: 当发送方发送数据包给接收方时,会为每一个数据包设置一个定时器,当在设定的时间内,发送方仍没有收到接收方的ACK信号,会再次发送该数据包,直到收到接收方的ACK信号或者连接已断开
(4)、校验信息: tcp首部校验信息较多,udp首部校验信息较少。上文部分协议简单讲
- IEEE 802.1A、IEEE 802.2
IEEE是英文Institute of Electrical and Electronics Engineers的简称,其中文译名是电气和电子工程师协会。IEEE 802规范定义了网卡如何访问传输介质(如光缆、双绞线、无线等),以及如何在传输介质上传输数据的方法,还定义了传输信息的网络设备之间连接建立、维护和拆除的途径。遵循IEEE 802标准的产品包括网卡、桥接器、路由器以及其他一些用来建立局域网络的组件。
IEEE802.1A —— 局域网体系结构
IEEE802.2 ——- 逻辑链路控制(LLC)- FDDI
光纤分布式数据接口(Fiber Distributed Data Interface)- PPP
点对点协议(Point to Point Protocol),为在点对点连接上传输多协议数据包提供了一个标准方法。- IP
互联网协议(Internet Protocol),为计算机网络相互连接进行通信而设计的协议。任何厂家生产的计算机系统,只要遵守IP协议就可以与因特网互连互通。IP地址具有唯一性,根据用户性质的不同,可以分为5类。- ICMP
控制报文协议(Internet Control Message Protocol)。TCP/IP设计了ICMP协议,当某个网关发现传输错误时,立即向信源主机发送ICMP报文,报告出错信息,让信源主机采取相应处理措施,它是一种差错和控制报文协议,不仅用于传输差错报文,还传输控制报文。- ARP/RARP
ARP (Address Resolution Protocol) 地址解析协议
RARP (Reverse Address Resolution Protocol) 反向地址解析协议- SMTP
简单邮件传输协议(Simple Mail Transfer Protocol),它是一组用于由源地址到目的地址传送邮件的规则,由它来控制信件的中转方式。SMTP协议属于TCP/IP协议簇,它帮助每台计算机在发送或中转信件时找到下一个目的地。通过SMTP协议所指定的服务器,就可以把E-mail寄到收信人的服务器上了。- SNMP
简单网络管理协议(Simple Network Management Protocol ),该协议能够支持网络管理系统,用以监测连接到网络上的设备是否有任何引起管理上关注的情况。- DNS
域名系统(Domain Name System),因特网上作为域名和IP地址相互映射的一个分布式数据库,能够使用户更方便的访问互联网,而不用去记住能够被机器直接读取的IP数串。通过主机名,最终得到该主机名对应的IP地址的过程叫做域名解析(或主机名解析)。DNS协议运行在UDP协议之上,使用端口号53。- FTP
文本传输协议(File Transfer Protocol),用于Internet上的控制文件的双向传输。同时,它也是一个应用程序Application)。基于不同的操作系统有不同的FTP应用程序,而所有这些应用程序都遵守该协议以传输文件。在FTP的使用当中,用户经常“下载”(Download)和“上载”(Upload)。“下载”文件就是从远程主机拷贝文件至自己的计算机上;“上载”文件就是将文件从自己的计算机中拷贝至远程主机上。- HTTP
超文本传输协议(HyperText Transfer Protocol),是互联网上应用最为广泛的一种网络协议。所有的WWW文件都必须遵守这个标准。它可以使浏览器更加高效,使网络传输减少。它不仅保证计算机正确快速地传输超文本文档,还确定传输文档中的哪一部分,以及哪部分内容首先显示(如文本先于图形)等。HTTP是一个应用层协议,由请求和响应构成,是一个标准的客户端服务器模型,是一个无状态的协议。